Navigating through modern network configurations often revolves around seamless access to device interfaces, with Winbox login standing out as a preferred choice for MikroTik RouterOS management. Whether you’re a network administrator or an enthusiast trying to manage your home network, understanding how to effectively log in to your MikroTik devices using Winbox unlocks powerful control and customization options. This guide aims to explore every nuance of Winbox login, from initial access to advanced security practices, equipping you with knowledge to optimize your network management experience.
Understanding Winbox Login — The Gateway to MikroTik RouterOS Configuration

Getting started with Winbox login is fundamental for anyone who wants to manage MikroTik routers effectively. Winbox serves as a versatile, Windows-based utility that provides graphical and command-line access to RouterOS devices, making network setup and troubleshooting more straightforward than ever. Knowing its significance and mechanics enables users to quickly troubleshoot, configure, and enhance network performance.
Before delving into the technicalities, it’s essential to grasp why Winbox login remains popular among network professionals. It offers real-time access without requiring complex web interfaces or SSH connections, ensuring streamlined management even in complex network environments. The process of logging in involves connecting your device to the same network, identifying your router, and authenticating credentials, which then grants you the control over various parameters of your network device.
Furthermore, understanding the Winbox login process can help diagnose problems like connectivity issues, unauthorized access, and configuration errors. Whether you’re using it for routine setups or critical troubleshooting, mastering how to log in efficiently creates a foundation for maintaining a secure and robust network. Now, let’s explore the step-by-step process of accessing your MikroTik device via Winbox.
Initiating Winbox Login — Connecting to Your Router
The first step in Winbox login is establishing a connection with your MikroTik device. When you launch Winbox, it automatically scans the local network for MikroTik routers. If your device appears in the list, select it directly; if not, you can input its IP address manually. This process may involve several preparation steps such as ensuring your PC and router are on the same subnet and that network cables are properly connected.
Once you identify the correct router, clicking on its entry will open the login window. The default port used by Winbox for connection is UDP 8291, but this can be customized for security reasons. Properly configuring your firewall to allow this port is vital, especially when managing remotely. Ensuring your network is configured to permit these connections is fundamental to access your router.
Security considerations also highlight the importance of changing default credentials as soon as possible. Many MikroTik devices come with factory usernames and passwords, typically “admin” and no password, which poses significant vulnerabilities. Setting strong, unique passwords during initial setup reduces risk and secures your Winbox login process. With the connection established, entering valid credentials grants access to the device’s configuration.
Troubleshooting Common Winbox Login Issues
During the login process, network professionals often encounter various issues that prevent successful access. Recognizing and resolving these can save time and prevent potential security vulnerabilities. Typical problems include IP conflicts, firewall blocks, or incorrect login credentials.
One common obstacle is incorrect username or password entry. When login fails, first verify your credentials, especially if the default settings have been changed. Resetting the device to factory settings can help regain access but should be a last resort due to potential data loss. Using alternative methods like SSH or WebFig can also assist in troubleshooting login issues if Winbox access remains unavailable.
Another significant challenge involves network restrictions, such as firewall policies blocking UDP port 8291 or misconfigured IP addresses. To troubleshoot, temporarily disable firewalls or adjust rules to allow Winbox connections. Additionally, router misconfiguration, such as disabled Winbox access in the IP firewall, can obstruct login attempts. Carefully checking the device’s firewall and access policies ensures smooth connectivity.
Securing your login process is equally critical. Unauthorized access risks are high if default or weak passwords are used. Implementing hard-to-guess passwords, enabling IP access permissions specifically for trusted administrators, and using VPNs for remote access greatly enhance security. Regularly updating RouterOS firmware is also recommended to patch vulnerabilities that could be exploited during login procedures.
Enhancing Winbox Login Security and Accessibility

Securing Winbox login is essential for protecting your network from unauthorized access and potential attacks. With the prevalence of cyber threats, setting up robust defenses around administrator access points significantly reduces vulnerability. This section discusses best practices to enhance security while maintaining ease of access for trusted users.
First, always replace default passwords immediately after initial device setup. A complex, unique password composed of a mix of characters substantially increases security. Additionally, limiting Winbox access to specific IP addresses through access rules is an effective security measure that prevents unwanted intrusion. in MikroTik, IP binding settings should be carefully configured to allow only trusted stations.
Furthermore, diversifying your access methods can significantly improve overall security. VPN tunneling, for example, allows you to connect remotely to your network securely without exposing Winbox to the public internet directly. Setting up a VPN server within your MikroTik device creates a safe pathway for administrators and reduces the risk of interception or brute-force attacks. Always remember that enabling two-factor authentication, where possible, adds extra security layers.
User management is also a cornerstone of secure Winbox login practices. Creating multiple user accounts for different administrative levels prevents over-privileging and facilitates accountability. Regularly reviewing access permissions and audit logs helps detect suspicious activities early. Combining these practices ensures that your network remains protected while accessible for those who need it.
Accessing Winbox Remotely — Best Practices and Considerations
Many administrators need to access their MikroTik routers remotely, which introduces specific challenges and risks. Enabling remote Winbox login provides convenience but must be balanced with security. A thoughtful approach involves configuring dedicated setups that restrict access to authorized personnel while minimizing exposure.
One fundamental practice is disabling direct Winbox access over the internet unless absolutely necessary. Instead, establish a VPN connection to securely access your internal network and subsequently login through Winbox as if on local LAN. This two-layer approach ensures sensitive configurations remain protected behind encrypted tunnels. MikroTik’s own router configurations support VPN setups like L2TP, PPTP, or OpenVPN, which, once properly configured, give safe remote access.
Another option for secure remote login is to change the default listening port from UDP 8291 to a non-standard port. This obscurity offers a layer of security by making it less obvious to attackers scanning for open ports. However, it is essential to document and remember the custom port, as forgetting it can lock you out of your device. Always test remote access considerably to verify that security measures do not inadvertently hinder legitimate uses.
It is also prudent to implement IP-based firewall rules restricting Winbox login attempts from untrusted sources and set up account lockouts for repeated failed login attempts. These measures help prevent brute-force attacks when providing remote access capabilities. Ultimately, balancing accessibility with security in Winbox login configuration ensures your network remains both manageable and safe from external threats.
Advanced Winbox Login Management — Tips for Power Users and Network Pros
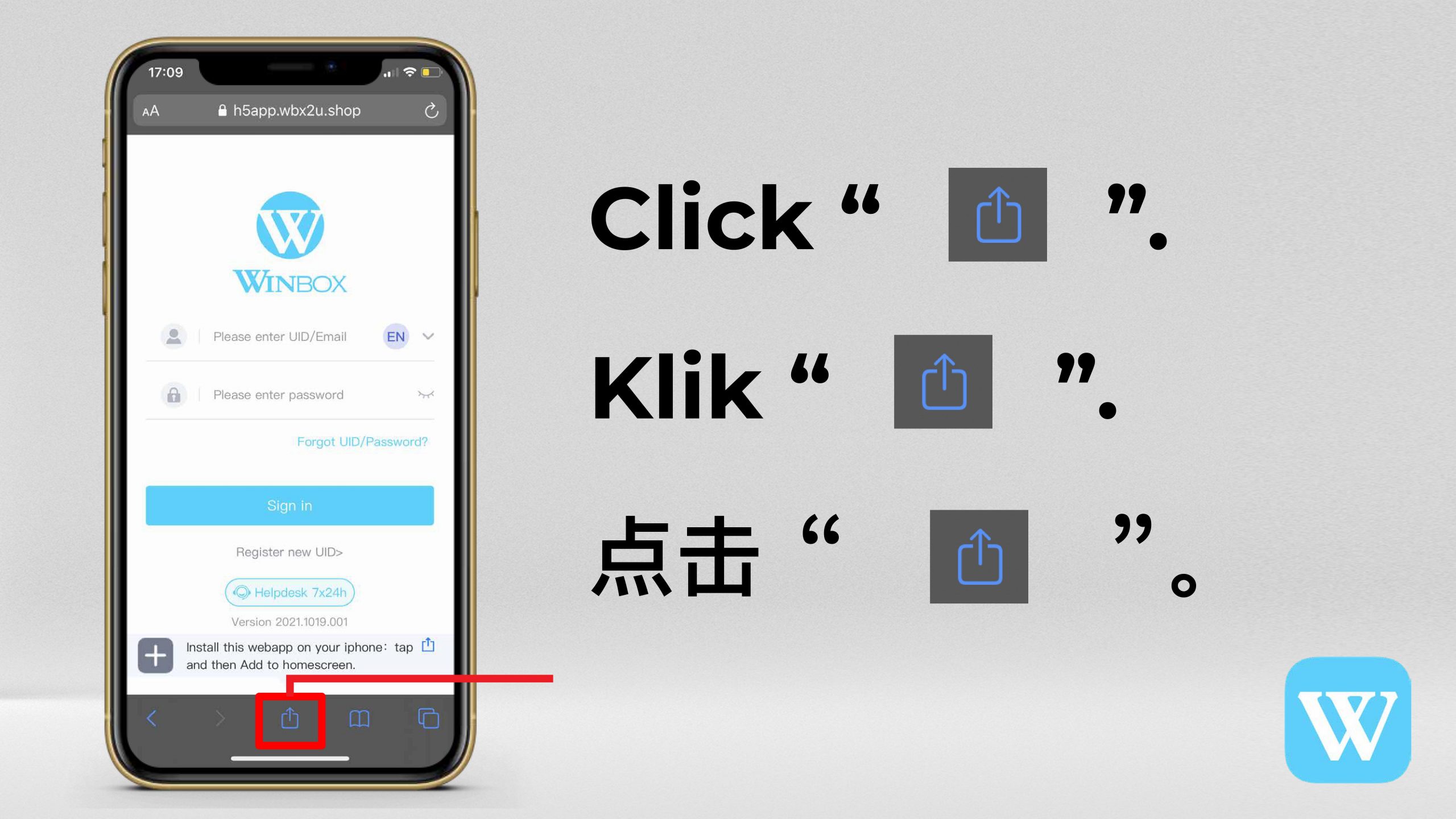
For seasoned professionals managing complex networks, mastering advanced Winbox login management can streamline operations, enhance security, and facilitate efficient troubleshooting. This section delves into tips and techniques that elevate your ability to control access, automate login processes, and maintain system integrity.
One advanced method is scripting routine login and configuration tasks through MikroTik’s scripting language or automation tools like Ansible. Automating repetitive procedures reduces manual errors and allows for quicker deployment of network policies. Incorporating encrypted scripts and secure credential storage safeguards sensitive information during automation routines. This approach is invaluable for managing large-scale networks with multiple MikroTik devices.
Additionally, utilizing user roles and permissions within MikroTik’s user management system allows granular control over who can login via Winbox and what actions they can perform. Assigning specific privileges based on job function ensures that users can only access necessary features, minimizing the risk of accidental misconfigurations. Regularly auditing user privileges and logs helps detect anomalies promptly.
Another technique involves monitoring Winbox login activity through system logs, which provides insights into access patterns, potential brute-force attempts, and unauthorized login attempts. Setting up alert mechanisms for suspicious activity ensures rapid response and mitigation. These practices—combined with up-to-date firmware, strong passwords, and layered security—enable power users to maintain resilient network environments capable of handling sophisticated threats.
Conclusion
Mastering Winbox login is a fundamental step for anyone managing MikroTik RouterOS devices, offering a potent interface for configuring, troubleshooting, and securing networks. From initial connection setups to implementing advanced security measures, understanding each facet ensures reliable and safe network operations. Effective management entails not only knowing how to access your device but also proactively securing the login process, controlling remote access, and leveraging automation and monitoring tools for optimal performance. As networks grow more complex, developing a comprehensive understanding of Winbox login procedures and best practices becomes crucial in maintaining a resilient and secure networking environment, empowering users to manage their MikroTik devices confidently and efficiently.
